

SecIron named as
Top 10 Mobile Application Security Solutions Providers
2024 by APAC CIO Outlook
Read more


End-to-End Solutions for Mobile Application Security
We protect mobile applications from cybercrime by deploying cutting-edge security solutions and doing our part to make the online world a safer place. SecIron helps you in keeping your business securely up and running, no matter what digital disruptions come your way.

Innovative solutions
Innovative and code-less solution and developments of mobile application security solutions that mitigates future potential threats with the latest multi-layered encryption, hardening injection protocols, and Runtime Application Self Protection (RASP) scanning to ensure utmost secure platform.

Proven expertise
Trusted by industry leaders, our proven expertise and in-depth industry know-how enable us to deliver tailored solutions that drive results and exceed expectations. With a track record of success and a passion for innovation, we bring unparalleled value to our clients and help them stay ahead in a rapidly evolving business landscape.

Accelerate transformation
We empower businesses to adapt quickly and securely in a constantly changing environment. With a deep understanding of interdependencies and downstream impacts, we enable teams to seamlessly adopt and integrate DevSecOps practices, resulting in robust and secure applications. Our solutions accelerate transformation, allowing businesses to stay ahead of the curve and achieve their goals with confidence.
Upcoming Events
Reduce Attack Surfaces and Take Control
Solutions That Help You Deploy Mobile Applications Faster and Secure
Mobile Application Security Assessment
Thorough Inspection of Mobile Application
Diagnose and identify vulnerabilities and remediation in mobile applications in preventing potential cybersecurity threats.

Mobile Application Hardening
Defend Applications Against Known & Unknown Threats
Manage, prevent, and protect against risks by deploying cutting-edge security that obfuscates, encrypts, and protects against app tampering, malware, reverse engineering, and other threats, effectively reducing attack surfaces exposure.
Mobile Application Real-Time Monitoring & Response System
All-in-One Monitoring and Defense Solution
Complete analysis and an information-critical dashboard with unified insights that deliver critical resource-based information in real-time.


Authenticate Digital Identity
Secure Digital Identity Authentication
Secure user identity, protect transactions and deploy best-in-class Dynamic Authentication Solution (DAS) for enterprise mobility management with ease.
Build Secure Apps to Prevent Reverse Engineering
SecIron embrace the Adaptive Security Architecture (ASA) principles, which aim to Prevent, Detect, Respond and Predict threats. This is achieved through a combination of continuous monitoring and threat intelligence, automation, integration and risk-based decision-making. In fact, our advanced solutions allow for seamless integration with Continuous Integration and Continuous Deployment (CI/CD) pipelines.
At SecIron, our unwavering mission is to provide clients with the most resilient, responsive and effective security solutions, fortified to combat today’s ever-evolving cyberthreats.
Predicts security threats before they happen, allowing businesses to fix them proactively. Scan the app with OWASP, CVE and CWE standard and get a quick report with remediation.
- Hardens system
- Isolate system
- Prevent attacks
Protects mobile apps from known and unknown attacks (static & dynamic) for continuous security.
- Detect incidents
- Confirm and prioritise risk
- Contain incidents
Providing businesses security dashboard to get real-time insights to guard mobile apps.
- Remediate
- Design / Model policy change
- Investigate incidents
- Do retrospective analysis
Automatically stops security threats with minimal user disruption.
- Anticipate threats / attacks
- Do risk-prioritised exposure assessment
- Baseline system and security posture
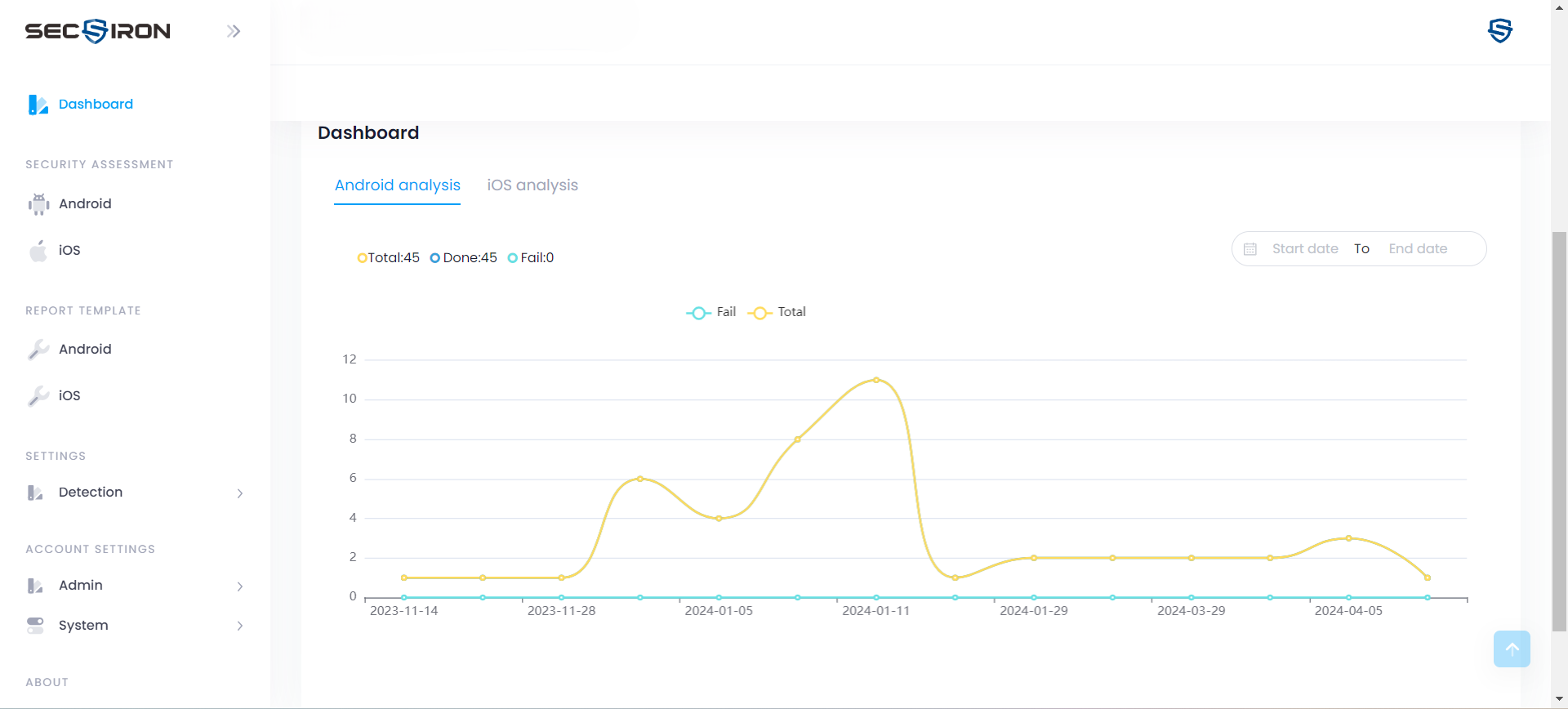
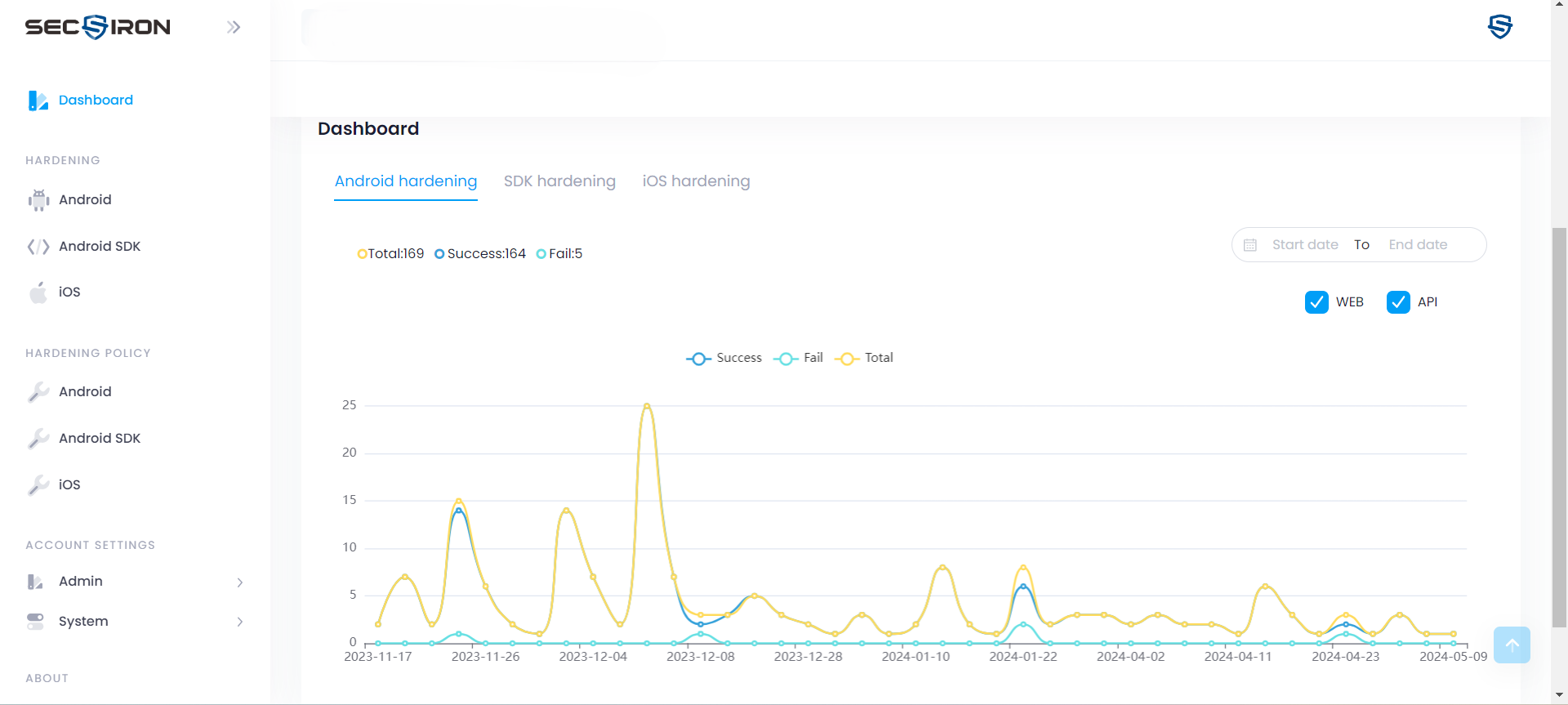
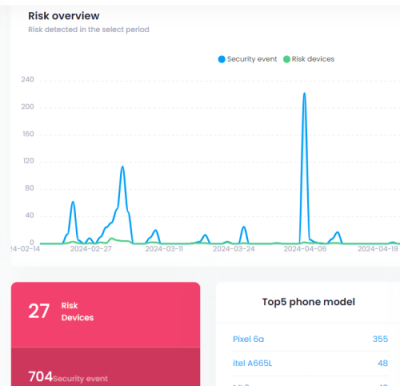
Ready to launch a secure app?
From deployment to security and beyond, SecIron helps you take you from visibility to action.
Recent News & Articles
-
Blog
-
Success Stories
-
Whitepapers & Guides
The mobile app security solution trusted by the world's most demanding customers
Harness our decade-long industry experience and ISO/IEC 27001 certification for unwavering reliability, exceptional performance, and the highest standards of privacy & security for customers worldwide.

